Managed Security Services

It’s common for small to medium-sized organizations to limit cybersecurity spending because of the mistaken belief that they are “too small to target.” But because these businesses lack the resources and experienced staff needed to defend themselves from new, sophisticated cyberattacks, they are in fact ideal targets. With a proven managed cybersecurity partner like SYS IT, however, any business can benefit from expert, enterprise-grade security services without fear of breaking their budget.
For a predictable, affordable monthly fee, Managed Security Services from SYS IT will protect your network, servers, data, and endpoints from every angle. Our experienced security technicians will implement solutions that not only protect you from advanced attacks like zero-day threats and ransomware, but also operate efficiently and consume minimal resources. By partnering with SYS IT for your security needs, you are getting an all-in-one solution to protect your data, customers, reputation, and profits while your workforce (remote or otherwise) remains productive.
Solutions Offered with our Managed Security Services Include:
Managed Next-Generation Firewall
- Capture Advanced Threat Protection (ATP) Service revolutionizes advanced threat detection and sandboxing with a cloud-based, multi-engine solution for stopping unknown and zero-day attacks at the gateway. Capture ATP blocks zero-day attacks before they enter your network. It lets you establish advanced protection against the changing threat landscape and analyze a broad range of file types.
- Real-Time Deep Memory Inspection (RTDMI) Detects and blocks malware that does not exhibit any malicious behavior or hides its weaponry via encryption. By forcing malware to reveal its weaponry into memory, the RTDMI engine proactively detects and blocks mass-market, never-before-seen threats and unknown malware, accurately utilizing real-time memory-based inspection techniques.
- Gateway Anti-Virus and Anti-Spyware Protection combines network-based anti-malware with a dynamically updated cloud database of tens of millions of malware signatures. This adds deep security protection against advanced modern threats continuously in real time. Dynamic spyware protection blocks the installation of malicious spyware and disrupts existing spyware communications.
- Intrusion Prevention Services (IPS) technology protects against worms, trojans, software vulnerabilities and other intrusions by scanning all network traffic for malicious or anomalous patterns, thereby increasing network reliability and performance.
- VPN enables remote users to securely connect and run any application on the company network. Users can upload and download files, mount network drives, and access resources as if they were on the local network.
Email Security and Protection
- Multilayered protection – Email security and protection leverages the same enterprise-class security and visibility used by some of the world’s largest and most security-conscious organizations in the world. It helps you protect your greatest security risk—your people. Our multilayered anti-virus, anti-spam, and phishing detection engines give you the best possible protection against malware-based and malware-free email threats. All your emails are scanned by our sophisticated engines. They quickly, accurately, and effectively capture and block all known viruses, malware, and ransomware. For even stronger protection, you can rely on our heuristics scanning. It discovers unknown email threats and protects you against these in real time.
- Advanced threat protection – Most attacks target people. They entice them to click on a link in an email or open an attachment. We leverage the advanced power of Targeted Attack Protection, our industry leading email analysis solution, to protect your people. This unique technology provides you with URL and attachment sandboxing analysis.
- Data Loss Prevention and Content Filtering – Helps you stay compliant. Our policy-driven DLP filter helps reduce your risk when your people make security and disclosure policy decisions. You can automatically identify and secure outgoing sensitive information. This includes PII, PHI, financial information, GDPR terms and many more with built-in term dictionaries and SmartSearch identifiers.
- Social Media Account Protection – We help you with social media account protection and compliance for up to three branded social media accounts. You can choose from Facebook, Twitter, YouTube and Google+. We help you monitor each account to prevent account hacking and protect from spam and malware being posted on your channels.
- Secure Email Communications – Securing emails that contain sensitive data is one of your top priorities. No one wants to face fines, bad press and loss of customer trust for losing confidential data or customer information. Our email encryption helps you reduce the potential negative impacts of data loss by automatically encrypting email.
- Email Continuity – Emergency inbox gives users automatic access to email when your cloud service provider or on-premise server is down. It keeps business email up and running at all times.
Extended Detection and Response (XDR)
- Secure XDR NGAV integrates multiple prevention technologies to maximize the points in which standard and zero day attacks can be terminated
- Immediately detects ransomware at the beginning of its cycle. With the ability to automatically respond, Secure XDR can stop the process before files or drives are encrypted
- Continuously monitors and profiles user activity to define a legitimate behavioral baseline and identify anomalous activity that indicates compromise of user accounts
- Plants various types of decoys across the environment to tempt attackers to get out of their hidings and reach out for what seems to be a valuable hunt and by doing that reveal their presence and former activities
Endpoint Detection and Response (EDR)
- Integrated proactive protection – Automated threat detection and protection across web, memory, application, and files applies adaptive detection techniques, including behavioral monitoring and cloud-based machine learning.
- Suspicious activity monitoring – Continuously analyzes endpoint processes, registry, file system, and network activity in the cloud using behavioral analysis and machine learning to pinpoint potential suspicious activity.
- Cloud sandbox – Deep analysis of unknown threats is done safely in the cloud, providing highly precise detection through threat intelligence, delivering actionable IoCs.
- Ransomware Rollback – Our Ransomware Rollback technology works in sync with suspicious activity monitoring to catch ransomware behaviors. If ransomware behaviors are detected, EDR activates the file backups process by encrypting and relocating the data for later restoration. The file backup process limits backup copies to just-intime encrypted files. With one click, incident response teams can reverse ransomware damage by rolling back affected files to their pre-attack state up to 72 hours before their compromise.
Virtual CISO
- Information security leadership and best practices regular knowledge sharing sessions
- Regular, detailed security assessments and penetration testing
- Social engineering defense training for staff
- A detailed security roadmap, IT security policy, compliance strategy, and more
- A single point of contact for security issues and interacting with security product vendors
- Managed Next Generation Firewall with Advanced Security Services
- And anything else you need to protect your data, people, revenue, and reputation
Advanced Threat Detection for Microsoft 365
SaaS Defense’s data-independent technology detects unknown threats that other solutions miss by analyzing the composition of a safe email, chat, or document rather than scanning for already known security threats.
Datto SaaS Defense does not rely on third-party software and is built from the ground up to prevent zero-day threats as soon as they are encountered, minimizing the time needed to detect an intrusion.
Cyber threats are not limited to just phishing emails — proactively protect your clients’ Microsoft 365 suite, including OneDrive, SharePoint, and Teams, from ransomware, malware, phishing, and BEC.
Configure customizable spam filtering with a single click and add another level of protection to your clients’ inbox.
Learn MoreDark Web Monitoring
A dark and dangerous place The Dark Web is made up of digital communities that sit on top of the Internet, and while there are legitimate purposes to the Dark Web, it is estimated that over 50% of all sites on the Dark Web are used for criminal activities, including the disclosure and sale of digital credentials. Far too often, companies that have had their credentials compromised and sold on the Dark Web don’t know it until they have been informed by law enforcement — but by then, it’s too late.
How does this happen? When your employees use their work email on third party websites, like the types listed below, it makes your business vulnerable to a breach. With our Dark Web Monitoring, we can detect if your company is at risk due to exposed credentials on those websites.
What you can do to protect your business? By utilizing Dark Web ID™, a combination of human and sophisticated Dark Web intelligence with search capabilities, you are able to identify, analyze and proactively monitor for your organization’s compromised or stolen employee and customer data.
Prevent: Attacks on networks may be inevitable, but proactive monitoring of stolen and compromised data allows you to respond to a threat immediately to prevent a major breach.
Report: With 80,000+ compromised emails daily, the platform provides extensive reporting capabilities to track and triage incidents.
Monitor:
Predict: Dark Web ID allows us to see industry patterns long before they become trends, and offers the intelligence to keep you and your employees more protected.
Learn MoreCompliance-as-a-Service
- Achieve and maintain compliance with HIPAA, GDPR, SOX, PCI, and any other major data security standards
- Benefit from regular, comprehensive risk assessments
- Easily generate documentation to prove compliance
- Improve your overall cybersecurity posture and reduce risk across the board
- Avoid costly fines, reduce insurance premiums, and prevent reputational damage
Vulnerability Management Services
- In-depth, regular scanning of your entire IT infrastructure, including external devices
- Continual discovery of virtualized assets, which addresses blind spots with always up-to-date asset inventories
- Programmable scanning cadence to align with compliance guidelines
- Severity risk-based scoring for efficient prioritization of remediation activities
- Accurate analysis of risk exposures within business context
- Fast response and remediation times against identified vulnerabilities
- Detailed stakeholder reporting that provides operational and executive metrics to accurately measure performance
- Easy compliance with data security regulations, including GDPR, HIPAA, and PCI DSS, preventing infraction fines and reputational damage
Proven Cybersecurity Posture
Time to Develop a Cybersecurity Strategy
With your current security architecture, budget, and personnel, what kinds of threats could you reasonably defend against? Many companies, both large and small, often overestimate their preparedness against cyber threats. A cyberattack is the ultimate test of the effectiveness of your current security architecture and response protocols. Organizations who are unaware of their true cybersecurity maturity and have no cybersecurity strategy are more likely to experience a devastating impact to their business. SYS IT recommends that you build your security strategy around the NIST cybersecurity framework. The National Institute of Standards and Technology (NIST) is trusted by the information security industry as a source of cybersecurity best practices. If you follow their guidelines, there’s a much better chance that you’ll be able to address cybersecurity challenges by accurately assessing your existing risk posture.
The five pillars are as follows:
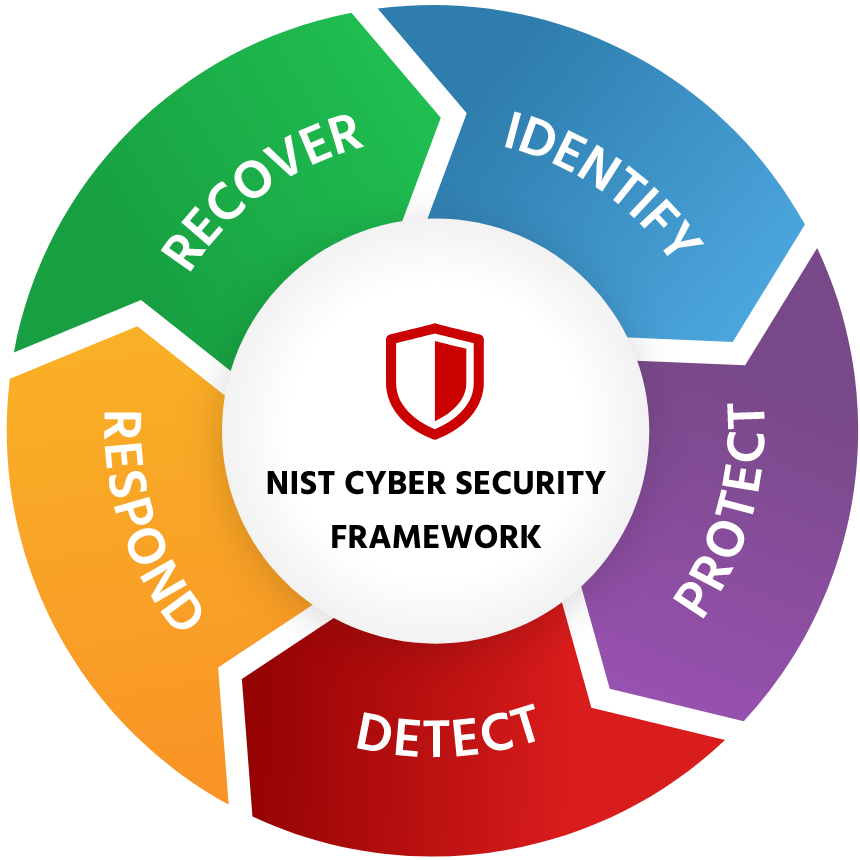
IDENTIFY: Use tools to identify every asset running in your development as well as their related vulnerabilities.
PROTECT: Take some basic security steps, such as protecting logins with multi-factor authentication and training employees to avoid phishing attempts.
DETECT: Set up monitoring solutions such as SIEM and IDS and tie them to your network and firewall. The former will detect intrusion attempts, the latter will block them.
RESPOND: Implement automation that flags incidents as worthy of human attention and directs ticket assignments accordingly.
RECOVER: Understand how long it takes you to recover normal functionality after a data breach or malware event—then understand how long it should take based on your SLAs.
Following these pillars will structure your organization’s security strategy and help you determine the elements most at risk from cyber-attacks. Executing on each of these pillars will create an effective, if not impervious, defensive cybersecurity strategy. When you have the defensive mechanisms and processes in place, you will be prepared for a determined attacker who may be able to get into your environment.
Prioritizing Security Based on the NIST Cybersecurity Framework
The NIST cybersecurity framework is used to create the structure of the cybersecurity matrix. On the x-axis, you have the pillars of framework: Identify. Protect. Detect. Respond. Recover. And the y-axis captures the organization’s assets that need to be assessed and protected: Devices. Applications. Network. Data. Users. After an assessment, you will earn a score that shows how well you have secured your business and highlights areas of the greatest need. You can take that information to create a cybersecurity strategy that can provide the greatest amount of protection within your budget.
NIST Cyber Security Framework
Identify
- Asset management
-
Business environment
- Governance
- Risk assessment
- Risk management strategy
Protect
- Awareness control
- Info protection and procedures
- Protective technology
- Next Generation Anti-Virus
- Next Generation Firewall
- Email Security and Protection
- Intrusion Prevention Services
Detect
- Anomalies and events
- Security continuous monitoring
- Detection process
- Endpoint Threat Detection
- Network and User Behavior Analysis
- Sandbox Analysis
Respond
- Response planning
- Communications
- Analysis
- Mitigation
- Improvements
- Endpoint Threat Detection and Response
Recover
- Recovery planning
- Improvements
- Communications
With Managed Security Services from SYS IT, you can expect:
- Industry best practices – a customized cybersecurity posture based on the NIST Cybersecurity Framework
- Leading-edge solutions – multiple layers of countermeasures protecting every avenue of attack into your systems
- Enterprise-grade tools – dark web monitoring, intrusion detection, advanced content-borne threat protection, and more to defend you against new and emerging attacks
- Detailed reporting – IT asset, policy, and credential management documentation to ensure clarity, oversight, and compliance
- Compliance consulting – expert assistance with achieving and maintaining compliance requirements for any digital security regulations and standards





