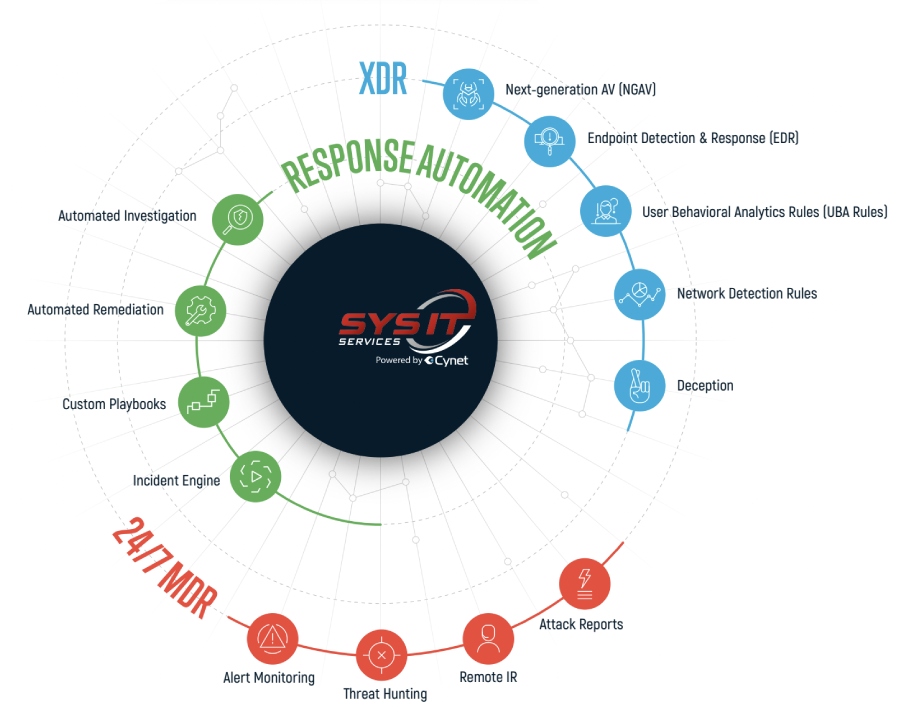
Extended Detection and Response (XDR)

Secure XDR: A Complete Cybersecurity Platform
Secure XDR: A Complete Cybersecurity Platform
End to End Autonomous Breach Protection
Extended Detection and Response (XDR)
Full visibility across endpoint, network and users, along with deception technology, to detect stealthy (and otherwise undetectable) attacks
Response Automation
Automatically launch responses that chain various investigation and remediation actions into a single flow that are initiated when high-risk alerts are triggered
Managed Detection and Response (MDR)
Cybersecurity experts monitor your environment 24/7 to ensure that no attacks are overlooked and provide expert advice and guidance
How Secure XDR Extends Threat Visibility
-
Download this FREE data sheet to learn more about Secure XDR: A Complete Cybersecurity Platform
- The Need for Better Threat Visibility
- The Right Set of Prevention and Detection Technologies
- Integrating Real-time signals
- Automated Response Actions
Prevent and Detect Attacks by Combining and Co-ordinating Key Security Controls
Secure XDR NGAV integrates multiple prevention technologies to maximize the points in which standard and zero day attacks can be terminated
- Identify and prevent execution of malware with known signatures
- Identify files with high similarity to know malware hashes
- Ensure only legitimate process can gain access to critical areas in memory
Secure XDR continuously monitors and profiles user activity to define a legitimate behavioral baseline and identify anomalous activity that indicates compromise of user accounts
- Define for each user or users’ group access policies for internal resources, on-prem or SaaS
- Verification message sent automatically via phone or email to validate the login nature and avoid false positives
- Triggers an alert on compromised user identity
Secure XDR immediately detects ransomware at the beginning of its cycle. With the ability to automatically respond, Secure XDR can stop the process before files or drives are encrypted
- Detect and block memory strings associated with ransomware so even unknown/obfuscated ransomware is exposed upon execution
- Protect the OS password vault so ransomware cannot harvest credentials and spread across the network
Plants various types of decoys across the environment to tempt attackers to get out of their hidings and reach out for what seems to be a valuable hunt and by doing that reveal their presence and former activities
- Plants text files containing false passwords along attackers’ potential routes. Any attempt to log in with these passwords triggers an alert
- Deception provides both off-the-shelf decoy files as well as the ability to craft your own

